Security Bulletin: Vulnerability analysis – DDC/AD
CertiSur response to Log4j vulnerability
CVE-2021-44228
Description / Impact
The threat, also named Log4Shell or LogJam, is a Remote Code Execution (RCE) class vulnerability. If an attacker manages to exploit it on a vulnerable server, they gain the ability to execute arbitrary code and potentially take full control of the system.
A wider description of the problem can be found in: https://www.lunasec.io/docs/blog/log4j-zero-day/
Product Versions
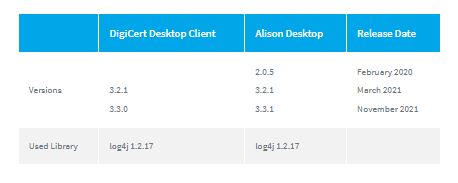
This analysis covers two different products: Alison-Desktop and DigiCert Desktop Client. We have evaluated the last most distributed versions of both products.
Vulnerability CVE-2021-44228
AD and DDC use a log4j version 1.x. This version is still very widely deployed, maybe several times more widely than version 2.x.
log4j 1.x does not offer a JNDI lookup mechanism at the message level, it does not suffer from CVE-2021-44228.
Another related vulnerability
- CVE-2021-4104 https://access.redhat.com/security/cve/CVE-2021-4104
We have done additional analysis on this fork and confirmed a new but similar vulnerability that can only be exploited by a trusted party. That vulnerability, related to JMSAppender, should require some special conditions to be exploited in any application. Specifically, any products that use Log4j 1.x are only affected if all of the following non-default configurations are in place:
- The JMS Appender is configured in the application’s Log4j configuration
- The javax.jms API is included in the application’s CLASSPATH
- The JMS Appender has been configured with a JNDI lookup to a third party. Note: this can only be done by a trusted user modifying the application’s configuration, or by trusted code setting a property at runtime .
AD and DDC don’t use an external application Log4j configuration file to be modified by an poisoning external application, and the default configuration doesn’t enable JMSAppender.
Recomended Action
Previous or Release Candidate versions of DigiCert Desktop Client (DDC) and Alison Desktop (AD) could include the log4j package in their distribution, but thanks to the version of the Java Virtual machine embedded in the aforementioned products and its configuration, the exploit of this vulnerability could not be achieved. However, and in case of any doubt we recommend the upgrade to DigiCert Desktop Client and Alison Desktop last versions on any branch that you are using.
CertiSur support can be contacted using our standard methods:
Email: support@certisur.com
Phone: https://www.certisur.com/en/contact-us/
© Copyright 2021 CertiSur S.A. All rights reserved.
CertiSur is a trademark or a registered trademark of CertiSur S. A. in Argentina and certain countries. All other company and product names and logos are trademarks or registered trademarks of their respective owners in certain countries.
Given the very nature of security vulnerabilities, security bulletins are intended to be kept to a small group of individuals. Security bulletins are to be distributed within your company only, and only on a need to know basis.
The information is provided “as is” by CertiSur without any representations, conditions and/or warranties of any kind, whether express, implied, statutory, by usage of trade, or otherwise. CertiSur specifically disclaims any and all representations, conditions, and/or warranties of merchantability, satisfactory quality, and/or fitness for a particular purpose. To the maximum extent permitted by applicable law, in no event will CertiSur be liable for any damages, losses or costs arising from your or any third party actions or omissions in connection with this bulletin. The only representations, conditions and/or warranties that may be applicable to any CertiSur products that you may have are those contained in the agreement pursuant to which you obtained a license for those CertiSur products.
